TinyML: Applications, Limitations, and It’s Use in IoT & Edge Devices
Unite.AI
AUGUST 29, 2023
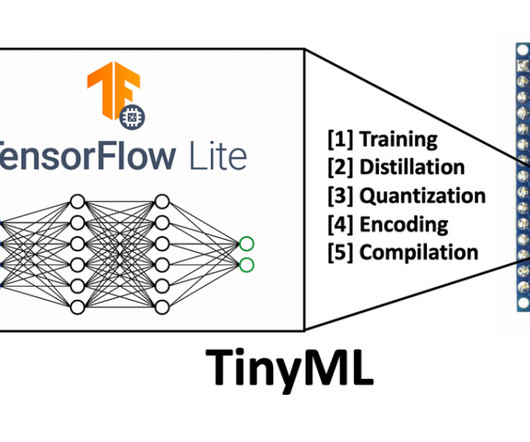
It would be safe to say that TinyML is an amalgamation of software, hardware, and algorithms that work in sync with each other to deliver the desired performance. Finally, applications & systems built on the TinyML algorithm must have the support of new algorithms that need low memory sized models to avoid high memory consumption.







Let's personalize your content